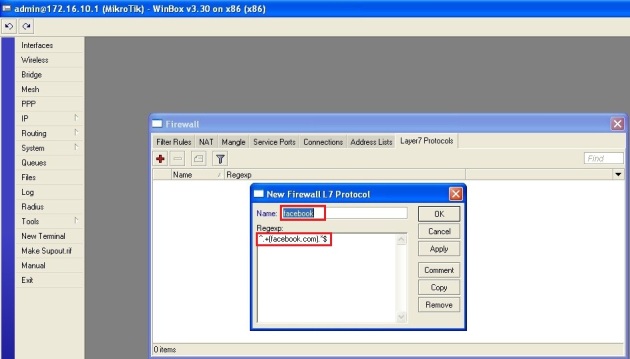
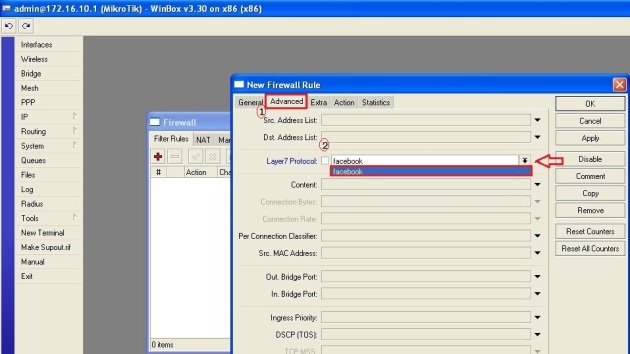
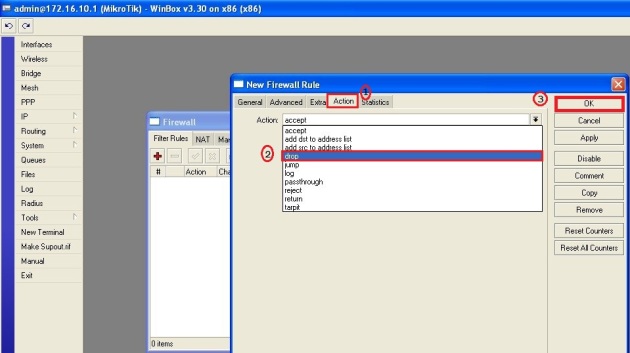
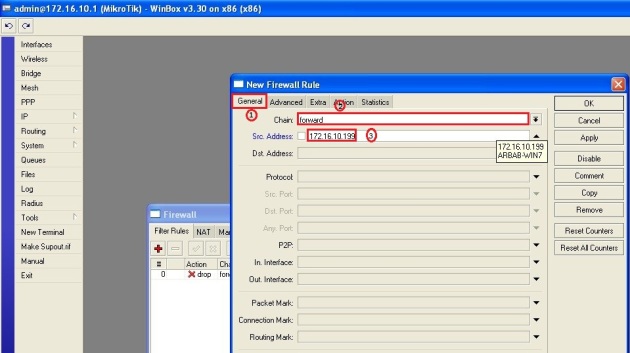
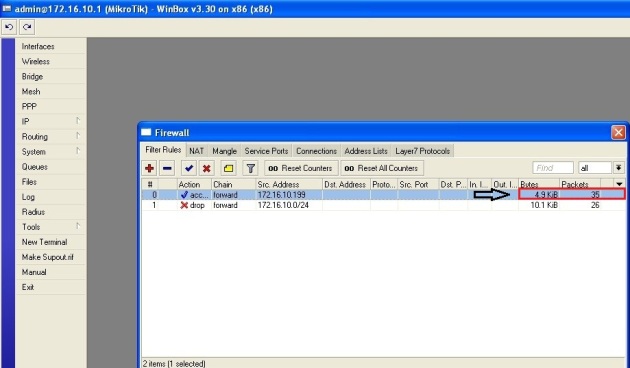
Beberapa hari yang lalu, saya selesaikan membuat konfigurasi network teman yang bikin warnet. Tentu saja ndak gratis… hahaha… Gambar networknya seperti di bawah ini. Konfigurasi yang dijelaskan disini hanya pada bagian Mikrotiknya saja. Pada bagian2 tertentu saya tambahkan sedikit penjelasan saja. Ya... setidaknya ini konfigurasi sebagai backup konfigurasi saya kedepannya... :) (Untuk hotspot dan squid bisa dilihat pada posting sebelumnya di blog ini).
Konfigurasi interface dan ip addressnya.
# jun/13/2014 21:00:49 by RouterOS 5.26
/interface ethernet
set 0 arp=enabled auto-negotiation=yes disabled=no full-duplex=yes l2mtu=1526 \
mac-address=4C:5E:0C:43:30:1A mtu=1500 name="ether1 WAN" speed=100Mbps
set 1 arp=enabled auto-negotiation=yes bandwidth=unlimited/unlimited \
disabled=no full-duplex=yes l2mtu=1522 mac-address=4C:5E:0C:43:30:1B \
master-port=none mtu=1500 name="ether2 SQUID" speed=100Mbps
set 2 arp=enabled auto-negotiation=yes bandwidth=unlimited/unlimited \
disabled=no full-duplex=yes l2mtu=1522 mac-address=4C:5E:0C:43:30:1C \
master-port=none mtu=1500 name="ether3 LAN" speed=100Mbps
set 3 arp=enabled auto-negotiation=yes bandwidth=unlimited/unlimited \
disabled=no full-duplex=yes l2mtu=1522 mac-address=4C:5E:0C:43:30:1D \
master-port=none mtu=1500 name="ether4 HOTSPOT" speed=100Mbps
/ip address
add address=192.168.1.2/24 disabled=no interface="ether1 WAN" network=\
192.168.1.0
add address=192.168.200.1/24 disabled=no interface="ether2 SQUID" network=\
192.168.200.0
add address=192.168.100.1/24 disabled=no interface="ether3 LAN" network=\
192.168.100.0
Untuk koneksi ke internet, menggunakan ADSL Telkom speedy. Modem speedy disetting sebagai bridge. Dan di mikrotik dibuat pppoe-client.
/interface pppoe-client
add ac-name="" add-default-route=yes allow=pap,chap,mschap1,mschap2 \
dial-on-demand=yes disabled=no interface="ether1 WAN" max-mru=1480 \
max-mtu=1480 mrru=disabled name="PPPoE TO INTERNET" password=******* \
profile=default service-name="" use-peer-dns=no user=\
172*******@telkom.net
Setting DNS-nya.
/ip dns
set allow-remote-requests=yes cache-max-ttl=1w cache-size=2048KiB \
max-udp-packet-size=4096 servers=202.134.1.10,8.8.8.8
Setting default routingnya.
/ip route
add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=192.168.200.2 \
routing-mark=markwebtosquid scope=30 target-scope=10
Setting NAT-nya. Ini nat agar client bisa connect ke internet.
/ip firewall nat
add action=masquerade chain=srcnat disabled=no out-interface=\
"PPPoE TO INTERNET" src-address=192.168.100.0/24
Ini NAT untuk client / IP-nya admin bisa connect ke modem speedy.
/ip firewall nat
add action=masquerade chain=srcnat disabled=no dst-address=192.168.1.0/24 \
out-interface="ether1 WAN" src-address=192.168.100.2
add action=masquerade chain=srcnat disabled=no dst-address=192.168.1.0/24 \
out-interface="ether1 WAN" src-address=192.168.200.2
Ini NAT untuk squid agar bisa connect ke internet.
/ip firewall nat
add action=masquerade chain=srcnat disabled=no out-interface=\
"PPPoE TO INTERNET" src-address=192.168.200.2
Ini destination NAT (DNAT) agar dari internet, bisa connect ke dalam squid. Istilah lainnya agar squid bisa diremote dari luar (internet ).
/ip firewall nat
add action=dst-nat chain=dstnat disabled=no dst-port=222 protocol=tcp \
src-address-list=half-trust to-addresses=192.168.200.2 to-ports=22
add action=dst-nat chain=dstnat disabled=no dst-port=8080 protocol=tcp \
src-address-list=half-trust to-addresses=192.168.200.2 to-ports=80
Untuk keamanan mikrotik menggunakan firewall filter. Pertama buat dulu kelompok IP address, seperti di bawah ini.
/ip firewall address-list
add address=3*.0.0.0/8 disabled=no list=half-trust
add address=118.**.0.0/16 disabled=no list=half-trust
add address=180.***.0.0/16 disabled=no list=half-trust
add address=180.***.0.0/16 disabled=no list=half-trust
add address=1**.0.0.0/8 disabled=no list=half-trust
add address=192.168.100.0/24 disabled=no list=lan
add address=192.168.200.0/24 disabled=no list=lan
Dengan adanya kelompok/group IP address seperti di atas, akan memudahkan dalam penerapan firewall filter.
/ip firewall filter
add action=drop chain=forward comment="drop invalid connections" \
connection-state=invalid disabled=no
add action=accept chain=forward connection-state=established disabled=no
add action=accept chain=forward comment="allow related connections" \
connection-state=related disabled=no
add action=accept chain=input disabled=no protocol=icmp src-address-list=lan
add action=drop chain=input disabled=no dst-port=!53,5353 \
in-interface="PPPoE TO INTERNET" protocol=tcp src-address-list=!half-trust
add action=accept chain=input disabled=no dst-port=!22,8291,8080,222 \
in-interface="PPPoE TO INTERNET" protocol=tcp src-address-list=half-trust
Setting firewall mangle, untuk meredirect web ke squid.
/ip firewall mangle
add action=mark-routing chain=prerouting comment="Redirect to Squid" \
disabled=no dst-port=80 new-routing-mark=markwebtosquid passthrough=yes \
protocol=tcp src-address=192.168.100.0/24
Setting firewall mangle, untuk me-mark trafik game online.
/ip firewall mangle
add action=mark-connection chain=prerouting disabled=no dst-port=\
1818,2001,3010,4300,5105,5121,5126,5171,5340-5352,6000-6152,6675,7777 \
new-connection-mark=GAME-ONLINE passthrough=yes protocol=tcp src-address=\
192.168.100.0/24
add action=mark-connection chain=prerouting disabled=no dst-port="7341-7350,74\
51,8085,9600,9601-9602,9300,9376-9377,9400,9700,10001-10011,10424" \
new-connection-mark=GAME-ONLINE passthrough=yes protocol=tcp src-address=\
192.168.100.0/24
add action=mark-connection chain=prerouting disabled=no dst-port=\
19101,22100,27780,28012,29000,29200,39100,39110,39220,39190,40000,49100 \
new-connection-mark=GAME-ONLINE passthrough=yes protocol=tcp src-address=\
192.168.100.0/24
add action=mark-connection chain=prerouting disabled=no dst-port=\
14009-14010,12683,5222,5223,9015,6203,6210,6217,6320,10360 \
new-connection-mark=GAME-ONLINE passthrough=yes protocol=tcp src-address=\
192.168.100.0/24
add action=mark-connection chain=prerouting disabled=no dst-port=\
47611,8401-8408,8000-8010,36456,36567,36570,37466 new-connection-mark=\
GAME-ONLINE passthrough=yes protocol=tcp src-address=192.168.100.0/24
add action=mark-connection chain=prerouting disabled=no dst-port=\
14300,14400-14406,14500-14600,10009,30001-30003,10089 \
new-connection-mark=GAME-ONLINE passthrough=yes protocol=tcp src-address=\
192.168.100.0/24
add action=mark-connection chain=prerouting disabled=no dst-port=\
13933,14001-14999,31928,31929,5222,5223,10074,28941 new-connection-mark=\
GAME-ONLINE passthrough=yes protocol=udp src-address=192.168.100.0/24
add action=mark-connection chain=prerouting disabled=no dst-port="1151,1293,14\
79,6100-6152,7777-7977,9401,9600-9602,12020-12080,30000,40000-40010" \
new-connection-mark=GAME-ONLINE passthrough=yes protocol=udp src-address=\
192.168.100.0/24
add action=mark-connection chain=prerouting disabled=no dst-port="42001-42052,\
10112,10201-10210,10294-10295,11100-11125,11440-11460,16400-16410,18061,19\
223" new-connection-mark=GAME-ONLINE passthrough=yes protocol=udp \
src-address=192.168.100.0/24
add action=mark-connection chain=prerouting disabled=no dst-port=\
8001-8010,40100-42000,12060-12070,27005-27015,31929,9647,42406-42441 \
new-connection-mark=GAME-ONLINE passthrough=yes protocol=udp src-address=\
192.168.100.0/24
add action=mark-connection chain=prerouting disabled=no dst-port=\
15100-15200,9001-9099,39030-39040,42106,42423,17327,17565 \
new-connection-mark=GAME-ONLINE passthrough=yes protocol=udp src-address=\
192.168.100.0/24
add action=mark-connection chain=prerouting disabled=no dst-port=\
9339,843,8890 new-connection-mark=GAME-FACEBOOK passthrough=yes protocol=\
tcp src-address=192.168.100.0/24
add action=mark-connection chain=prerouting disabled=no dst-port="10402,11011-\
11041,12011,12110,13008,13413,15000-15002,16402-16502,16666,18901-18909,19\
000" new-connection-mark=GAME-ONLINE passthrough=yes protocol=tcp \
src-address=192.168.100.0/24
add action=mark-packet chain=forward connection-mark=GAME-ONLINE disabled=no \
new-packet-mark=GAME-PAKET passthrough=yes
add action=mark-packet chain=forward connection-mark=GAME-FACEBOOK disabled=\
no new-packet-mark=GAME-PAKET passthrough=yes
Setting firewall mangle, untuk me-mark trafik hit squid
/ip firewall mangle
add action=mark-packet chain=postrouting disabled=no dscp=12 new-packet-mark=\
proxy-hit passthrough=yes
add action=mark-packet chain=prerouting disabled=no dscp=12 new-packet-mark=\
proxy-hit passthrough=yes
Tutup service port yang tidak digunakan.
/ip service
set telnet address="" disabled=yes port=23
set ftp address="" disabled=yes port=21
set www address="" disabled=no port=80
set ssh address="" disabled=no port=22
set www-ssl address="" certificate=none disabled=yes port=443
set api address="" disabled=yes port=8728
set winbox address="" disabled=no port=8291
Untuk pembagian bandwidth (queue), saya masih percaya sama queue simple.
/queue simple
add burst-limit=0/0 burst-threshold=0/0 burst-time=0s/0s direction=both \
disabled=no interface=all limit-at=0/0 max-limit=0/0 name=TOTAL \
packet-marks="" parent=none priority=1 queue=default-small/default-small \
target-addresses="" total-queue=default-small
add burst-limit=0/0 burst-threshold=0/0 burst-time=0s/0s direction=both \
disabled=no interface=all limit-at=0/0 max-limit=1M/1M name=GAME \
packet-marks=GAME-PAKET,dns-mark parent=TOTAL priority=8 queue=\
default-small/default-small target-addresses="" total-queue=default-small
add burst-limit=0/0 burst-threshold=0/0 burst-time=0s/0s direction=both \
disabled=no interface=all limit-at=0/0 max-limit=10M/10M name=HIT-PROXY \
packet-marks=proxy-hit parent=TOTAL priority=1 queue=\
default-small/default-small target-addresses="" total-queue=default-small
add burst-limit=0/0 burst-threshold=0/0 burst-time=0s/0s direction=both \
disabled=no interface=all limit-at=0/0 max-limit=256k/512k name=admin \
packet-marks="" parent=TOTAL priority=8 queue=default-small/default-small \
target-addresses=192.168.100.2/32 total-queue=default-small
add burst-limit=0/0 burst-threshold=0/0 burst-time=0s/0s direction=both \
disabled=no interface=all limit-at=0/0 max-limit=256k/440k name="User 1" \
packet-marks="" parent=TOTAL priority=8 queue=default-small/default-small \
target-addresses=192.168.100.3/32 total-queue=default-small
add burst-limit=0/0 burst-threshold=0/0 burst-time=0s/0s direction=both \
disabled=no interface=all limit-at=0/0 max-limit=256k/440k name="User 2" \
packet-marks="" parent=TOTAL priority=8 queue=default-small/default-small \
target-addresses=192.168.100.4/32 total-queue=default-small
add burst-limit=0/0 burst-threshold=0/0 burst-time=0s/0s direction=both \
disabled=no interface=all limit-at=0/0 max-limit=256k/440k name="User 3" \
packet-marks="" parent=TOTAL priority=8 queue=default-small/default-small \
target-addresses=192.168.100.5/32 total-queue=default-small
add burst-limit=0/0 burst-threshold=0/0 burst-time=0s/0s direction=both \
disabled=no interface=all limit-at=0/0 max-limit=256k/440k name="User 4" \
packet-marks="" parent=TOTAL priority=8 queue=default-small/default-small \
target-addresses=192.168.100.6/32 total-queue=default-small
Ini script untuk memantau squid, jika squid tidak connect, secara otomatis trafik web tidak akan melewati proxy squid, melainkan langsung menuju ke internet. Dengan demikian client tidak akan terdisconnect.
/system script
add name=down policy=\
ftp,reboot,read,write,policy,test,winbox,password,sniff,sensitive,api \
source=":log info \"Squid Proxy Server is not responding. Please Check Con\
nectivity\"\r\
\n/ip firewall mangle disable [find comment=\"Redirect to Squid\"]"
add name=up policy=\
ftp,reboot,read,write,policy,test,winbox,password,sniff,sensitive,api \
source=":log info \"Squid Proxy Server is OK.\"\r\
\n/ip firewall mangle enable [find comment=\"Redirect to Squid\"]"
/tool netwatch
add comment="Cek Squid" disabled=no down-script="/sys script run down" host=\
192.168.200.2 interval=45s timeout=1s up-script="/sys script run up"
Settingan lainnya.
/system clock
set time-zone-name=Asia/Makassar
/system identity
set name=MikroTik
/system ntp client
set enabled=yes mode=unicast primary-ntp=152.118.24.8 secondary-ntp=\